With Update 4’s exciting new cloud features, there are settings within AWS and Azure that you should familiarize yourself with to help negate some of the egress traffic costs, as well as help with security.
Right now, let’s talk about the scenarios where:
- You are backing up Azure/AWS instances, utilizing Veeam Backup & Replication with a Veeam Agent, while utilizing Capacity Tier all inside of AWS/Azure
- You have a SOBR instance in AWS/Azure and utilize Capacity Tier
- When N2WS backup and recovery/Veeam Availability for AWS performs a copy to Amazon S3
- If Veeam is deployed within AWS/Azure and you perform a DR2EC2 without a proxy or DR2MA
In AWS, by default, all traffic written into S3 from a resource within a VPC, like an EC2 instance, face egress costs for all these scenarios listed above. By default, when we archive data into S3 or do a disaster recovery to EC2, where Veeam uploads the virtual disk into S3, so AWS can convert to Elastic Block Store (EBS) volumes (AWS VMimport), we face an egress charge per GB. There is the option to utilize a NAT gateway/instance, but again there is a price associated with that as well.
Thankfully, there is an option that you could enable, which is basically the “don’t charge me egress!” button. That feature is called VPC Endpoints for AWS and VNet Service Endpoints for Azure.
Limit AWS egress costs
“A VPC Endpoint enables you to privately connect your VPC to supported AWS services and VPC Endpoint services powered by PrivateLink without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. Instances in your VPC do not require public IP addresses to communicate with resources in the service. Traffic between your VPC and the other service does not leave the Amazon network”.
You simply enable VPC Endpoints for your S3 service within that VPC and you will no longer face egress cost when an EC2 instance is traversing data into S3. This is because the EC2 instance doesn’t need a public IP, internet gateway or NAT device to send data to S3.
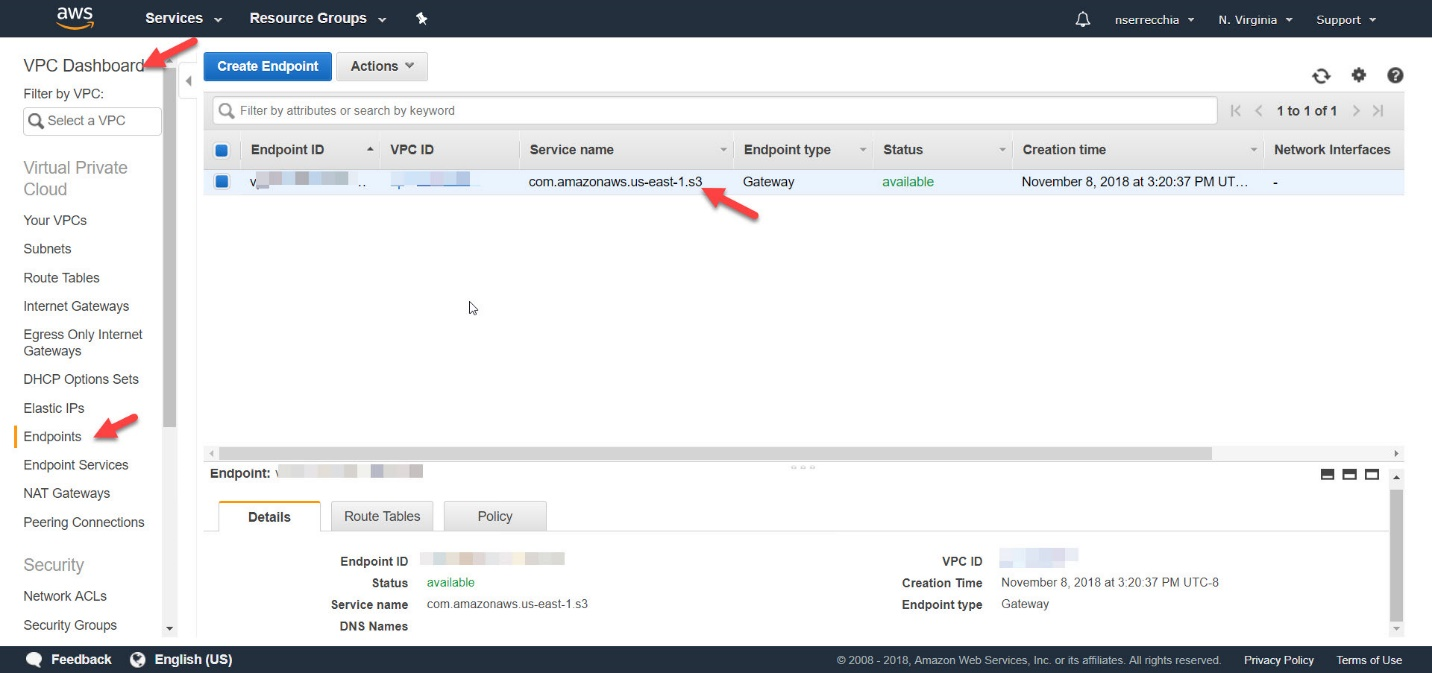
Now that you enabled the VPC Endpoint, I highly recommend that you create a bucket policy to specify which VPCs or external IP addresses can access the S3 bucket.
Limit Azure egress costs
Azure handles the egress costs from their instances into Blob in the same manner AWS does, but with Azure the nomenclature is different, they use VNets instead of VPCs and they too have a feature that can be enabled at the VNet level: VNet Service Endpoints.
“Virtual Network (VNet) service endpoints extend your virtual network private address space and the identity of your VNet to the Azure services, over a direct connection. Endpoints allow you to secure your critical Azure service resources to only your virtual networks. Traffic from your VNet to the Azure service always remains on the Microsoft Azure backbone network.”

With Azure, you can then setup a firewall within the storage account to limit internet access to that resource.
Again, this is for instances hosted within a VNet or VPC talking to their respected object storage within the same region, not on-premises to an S3/Azure storage account.
Source: Veeam

